How to detect and stop SMS pumping fraud
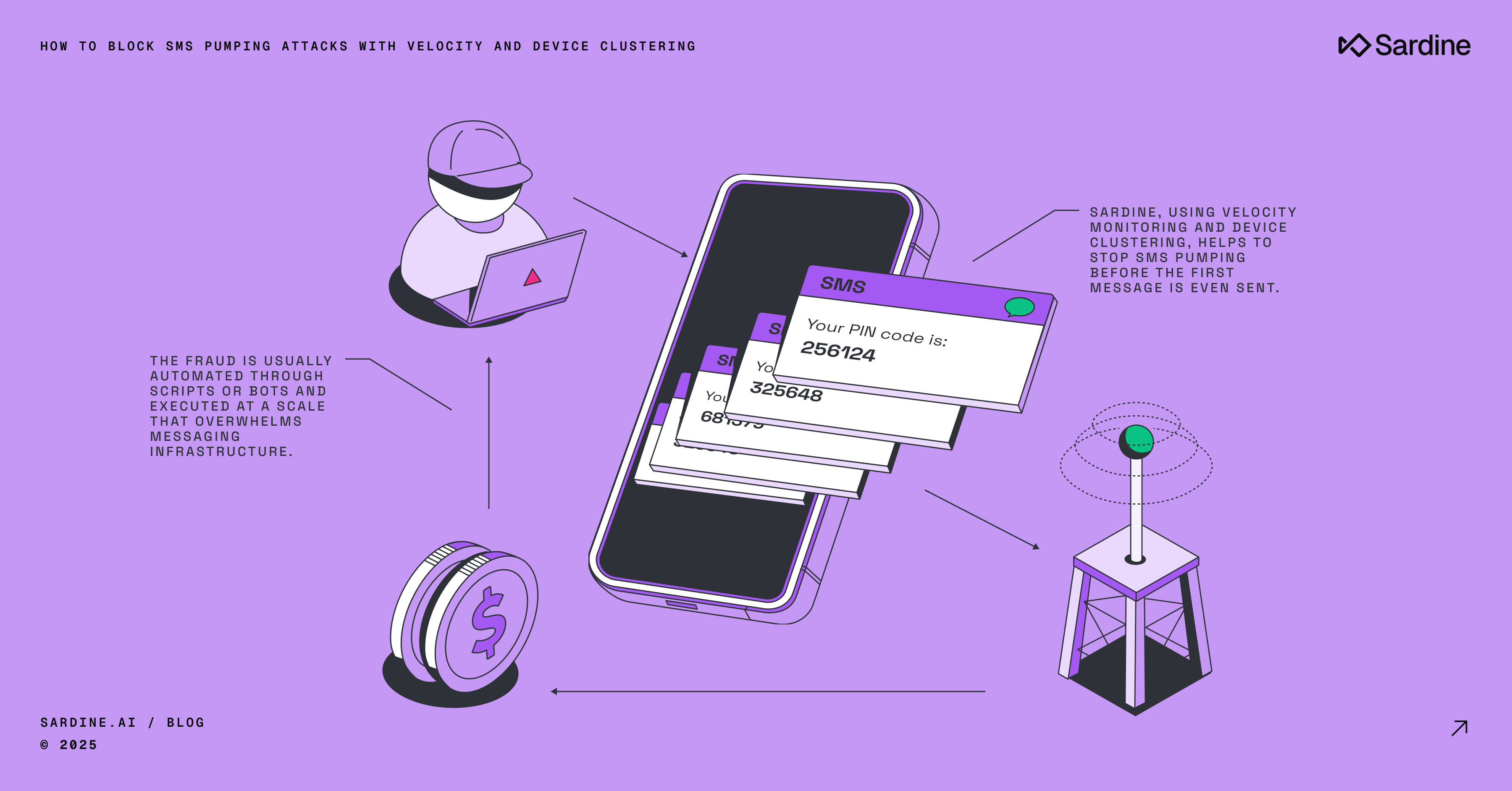
SMS pumping is a rapidly growing fraud attack exploit that often blindsides risk teams, especially in the financial services industry.
Fraudsters will exploit common UX flows like OTP and text 2FA requests during onboarding to trigger thousands of texts to premium-rate numbers they control. At first glance, it looks like an influx of new customers, but really it's fraudsters profiting by sending you fake traffic, while leaving your company holding the bag for the telecom bill.
These attacks move quickly and at scale, so even a single incident can cause significant losses. Yet risk teams miss them because their solutions are tuned to detect fraud, not platform abuse.
That’s why SMS pumping has become such a dangerous blind spot for fintechs and marketplaces. Luckily, SMS pumping can be stopped with the right signals.
What is SMS pumping?
SMS pumping is an attack where fraudsters exploit OTP and/or 2FA text message requests to generate high volumes of SMS traffic that the business ends up paying for. The goal isn’t to do an account takeover or to launder funds. It’s to route text messages to premium-rate numbers they control and skim a share of the fees. While this exploit may seem benign at first glance, it can result in tens of thousands of dollars in losses within minutes.
This scheme goes by many names, including SMS toll fraud, artificially inflated traffic (AIT), international revenue share fraud (IRSF), fake OTP abuse, or 2FA charging, but the mechanics are very similar:
- Fraudster finds an exposed SMS trigger that doesn’t have rate limits or throttling.
- They provision a block of premium-rate numbers through a shady carrier or SIM farm.
- Bots and/or scripts are used to initiate thousands of fake requests, often distributed through proxies or device emulators to avoid simple filters, as very few companies risk-score the OTP/2FA requests.
- Each request kicks off an API call to your SMS aggregator, which treats it like normal traffic and routes it downstream.
- Messages get funneled to the premium-rate numbers. Sometimes they terminate to a real SIM in a rack. Other times, the carrier just fakes delivery receipts.
- Billing flows back up the chain: your platform pays the SMS provider, the provider pays the carrier, and the carrier shares revenue with the fraudster.
- From your side, the telemetry looks clean: OTPs were “sent,” no logins failed, no customers complained. All you see is an unexpected surge in SMS volume.
.png)
Who does SMS pumping fraud impact?
SMS pumping fraud impacts several different parties: the businesses that are targeted, the CPaaS providers that deliver the traffic, the telcos that carry it, and the fraud and risk teams that are asked to answer for it.
It starts with the businesses themselves, because they are the ones left paying the bill. Every fake OTP request still gets invoiced by the SMS provider, which means fintechs and marketplaces absorb the cost directly.
The pain then moves to CPaaS providers. They may pass those costs through, but if customers continue to see six-figure invoice spikes without warning, they push back. Some churn. Others demand stronger controls. So while CPaaS vendors might not pay per message, they end up paying in customer satisfaction and retention.
That pressure eventually reaches the telcos. Enterprises rarely buy SMS directly from carriers, but when trust in SMS as a channel erodes, the volume that flows through CPaaS providers to telcos declines. Over time, that puts long-term telecom revenue at risk.
The fraud and risk teams are left in the middle. They are held accountable for why controls missed the abuse, even though their systems were never built to detect SMS pumping in the first place.
Finally, this can impact your customers in a significant way, where the attack has a high enough velocity to jam up the OTP/2FA funnels and cause failures or error messages for your real customers trying to get through an OTP/2FA step-up. This can not only cause a poor UX, but can even lead to churn.
How to detect SMS pumping attacks
Most risk teams miss SMS pumping because it doesn’t look like fraud in the traditional sense.
There are no unauthorized activity disputes, no synthetic identities, no user complaints. OTPs get “sent,” traffic looks clean, and dashboards show activity. Standard fraud rules are tuned for account takeovers or payment abuse, not for infrastructure abuse hiding in what looks like normal usage.
By the time someone asks why SMS invoices spiked, the damage is already done. On top of this, very few companies run decision logic on their OTP/2FA triggers, as they believe the OTP/2FA is all the logic needed.
If you want to catch it earlier, these are the tells worth watching:
Velocity anomalies
Real users do not hit OTP endpoints consecutively at machine speed. If one device or subnet fires hundreds of requests in minutes, that’s probably a bot attack. Use adaptive thresholds that shift with time of day, segment, and journey.
Bot signatures
Do not just infer automation from speed. Identify it. Sardine can detect 17+ automation frameworks, including Selenium, Playwright, and Stagehand. Combine signature hits with cadence, headless flags, and scriptable browser traits.
Device and network tells
Normal customers don’t typically go out of their way to hide their true IP and location. Using residential proxies can be a flag, especially when paired with other signals like bot or emulator use. Suspicious device attributes are another giveaway, like if the timezone country does not match the device’s GPS data, or the same fingerprint appears across multiple users.
Completion ratios
In a healthy funnel, sends turn into verifications. In pumping, sends spike and completions flatline. Track send to verify and send to session-continuation by prefix, route, and journey.
Destination patterns
Watch where requests land. Clustering in high-cost prefixes or geos where you have a small user base is a tell. Monitor MCC/MNC, number ranges, route shifts, and cost per verified user.
Throttling
Use your OTP/2FA/SMS providers' guardrails whenever possible, or use internal systems to ensure you leverage throttling technology to prevent rapid API call volumes through rate limiting. This is the same technology strategy you would be using for DDOS attacks
Connections graph
Fraudsters typically spread activity across what look like different accounts, but the signals connect if you map them. Shared IPs or IP ranges are a common link, as are device fingerprints reused across accounts. When one group of linked accounts is responsible for a disproportionate share of OTP requests, it’s likely you are looking at a coordinated attack.
.png)
What to do if you’ve already been hit
The best strategy against SMS pumping is stopping it before it takes hold. But if your organization has already been impacted, there are a few steps that can help limit the damage and pass liability back up the chain:
- Dispute charges. Contact carriers and request reversals for fraudulent traffic. In many cases, this passes liability to the carriers.
- Report the numbers. Forward suspicious numbers via script to 7726 (SCAM) so they can be flagged and blocked.
- Escalate if needed. In large-scale attacks, the FCC can get involved, and in many cases they will hold carriers liable.
- File reports. If your organization falls victim, file with the FTC to initiate a number takedown. This helps prevent those numbers from being recycled in future attacks.
While these measures will not stop an attack in motion, they can reduce the financial hit.
Why Sardine stops what other tools miss
Legacy systems miss these attacks because they lean too much on blocklists and static rules. They can stop known patterns, but anything new slips right through. SMS pumping takes advantage of that gap.
Sardine changes this up with a data-centric approach:
- We go deep into device and behavior data to surface the subtle signals others miss.
- We have the ability to quickly detect automation systems like bots, scripts, and agentic AI agents that are being used to facilitate this exploit through the use of proprietary behavioral tracking technology.
- We break down silos so all the data across the customer journey feeds into one complete view of risk.
- With unified signals, suspicious connections and coordinated activity become visible.
- Our Anomaly Engine monitors live traffic and flags unusual patterns as soon as they appear.
- Our AI then generates rule suggestions to stop those threats, cutting the time it takes your team to respond.
.png)
This approach enabled us to help one of our marketplace customers when they were hit with a fraud ring. Sardine flagged the activity as high risk within 250 milliseconds. Out of millions of risk decisions, only 0.068% were overturned by human reviewers.
.png)
If you’re dealing with large-scale fraud attacks, we can help you shut them down before they impact your business. Contact us to schedule a demo.