The new disputes rules from Visa: VAMP and enumeration attacks
Visa has officially launched a new fraud and dispute monitoring framework, the Visa Acquirer Monitoring Program (VAMP).
Visa is updating the requirements for the Visa Acquirer Monitoring Program (VAMP), consolidating the existing VAMP, Visa Fraud Monitoring Program, and Visa Dispute Monitoring Program into a single global program. Updates to the program thresholds will be effective June 1, 2025.
Each month, Visa monitors fraud, dispute, and enumeration levels and identifies acquirers or merchants that exceed monthly VAMP thresholds. Entities identified as exceeding program thresholds are required to implement risk mitigation control measures.
This post outlines the key aspects of VAMP, what’s changed, how it affects merchants and acquirers, and what fraud teams can do to adapt.
What is VAMP?
The core program metric is a single, count-based ratio (VAMP ratio) that includes key components of fraud and disputes on card-not-present VisaNet transactions (domestic and cross-border).
VAMP Ratio = Count of [Fraud (TC40) + Disputes (TC15)] ÷ Count of Settled Transactions (TC05)
VAMP Ratio has additional criteria: Excludes disputes resolved through pre-dispute solutions and excludes TC 40 fraud qualified for Compelling Evidence 3.0.
Previously, Visa tracked disputes and fraud separately under VDMP and VFMP. VAMP consolidates them into one measure. This creates a simpler compliance framework, but also increases the risk of double-counting fraud-related disputes unless you take steps to mitigate it.
Key changes under VAMP
Program thresholds
An acquirer’s portfolio is identified as Above Standard if its VAMP ratio is ≥50bps and as Excessive if ≥70bps; both identification levels have the same minimum 1500 monthly count of fraud and disputes to enter the program.
If acquirer is not Above Standard or Excessive, then the following Excessive Merchant performance thresholds apply:
Enumeration attacks now monitored
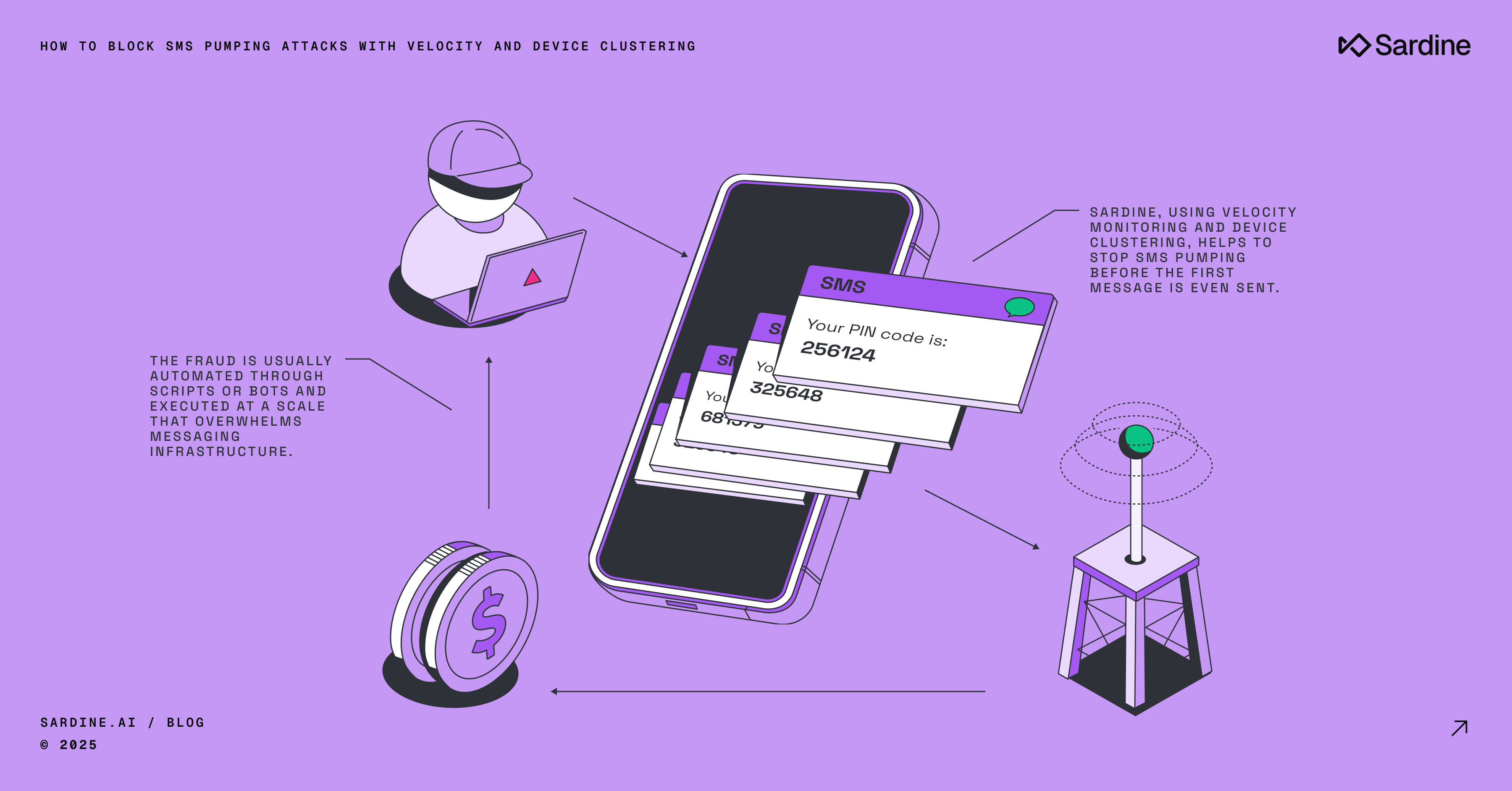
Visa will now track enumeration attacks directly as part of its VAMP evaluation. Enumeration occurs when fraudsters automate card-not-present authorization attempts using large sets of PANs, expiration dates, and CVVs to test for valid combinations.
VAMP requires acquirers to take proactive steps to prevent merchants from exceeding enumeration thresholds:
- VAMP Enumeration Ratio, defined as [Count of Enumerated Authorization Transactions (Approved + Declined)] ÷ [Count of Authorization Transactions (Approved+ Declined)], ≥ 2000 bps
- Minimum VAMP Enumeration Transaction Count, defined as Enumerated Transactions (Approved + Declined), ≥ 300,000
Changes to RDR, CDRN, and Compelling Evidence 3.0
Under VAMP, Visa has changed how it treats fraud and dispute signals resolved through its standard resolution tools.
RDR and CDRN no longer suppress TC40s, so fraud reports will still count toward your fraud ratio. However, they still cancel out TC15s for both fraud and non-fraud cases, reducing your dispute volume. That makes them less effective at managing fraud than they were under previous programs, but they remain useful for avoiding double-counting when both fraud and dispute would otherwise apply.
Compelling Evidence 3.0, submitted through Order Insight and accepted by the issuer, is now the only way to suppress TC40s and fully remove the fraud signal from VAMP calculations.
What this means for fraud teams
VAMP raises the bar for how fraud and disputes are tracked, measured, and penalized. For ecommerce merchants and payment processors, the margin for error is getting smaller.
- For merchant fraud teams, the focus needs to shift beyond loss prevention to signal control. Enumeration traffic, unresolved disputes, and unsubmitted CE can all contribute to VAMP ratios. Each missed signal increases the chance of excessive classification, even if your chargeback rate looks fine on paper.
- For acquirers, the exposure is now collective. A single merchant’s fraud and dispute performance can push your portfolio above threshold. That means closer monitoring, earlier intervention, and clear guidance on how merchants should be using tools like RDR, CDRN, and CE 3.0.
Across both sides, the takeaway is the same: VAMP compresses the timeline and tolerance for error. Staying compliant means getting proactive with signal quality, resolution speed, and cross-functional ownership.
Best practices for staying compliant under VAMP
1. Monitor authorization traffic for enumeration patterns
Look beyond chargebacks. Track spikes in declines, repeated authorization attempts with similar BINs, and velocity against a single issuer or card range. Enumeration risk isn't always visible in post-transaction data, you need to catch it upstream.
2. Tune decline logic without overblocking
Set velocity and threshold rules that detect bots, but avoid rules that penalize legitimate users in high-volume flows. Use device and behavioral signals to enrich decisioning, not just transaction metadata.
3. Use RDR and CDRN to suppress disputes early
Automate RDR enrollment where possible and respond quickly to CDRN alerts. These services won’t stop TC40s, but they can eliminate TC15s and reduce your dispute count in VAMP.
4. Implement CE 3.0 workflows for fraud rebuttals
Make sure your team can collect and submit Compelling Evidence 3.0 quickly, not after a case has aged out. Use Order Insight integration to surface device fingerprints, behavioral consistency, and matching geolocation. This is your only path to suppress TC40s.
5. Get acquirer visibility into VAMP signals
If you're a merchant, ask your acquirer to share your TC40s, TC15s, and enumeration ratios. You can't fix what you can't see. If you're an acquirer, make it easy for merchants to see what you're seeing.
6. Align ownership across fraud, disputes, and network compliance
Fragmented ownership slows down resolution. Make sure the teams responsible for fraud prevention, chargebacks, and CE submission are operating from the same thresholds, tools, and VAMP timeline.
7. Review VAMP status monthly, not quarterly
Don’t wait for fines to appear. Use internal reporting or acquirer dashboards to track dispute ratio trends and fraud classification risk in near real time. Set internal alerting thresholds below Visa’s thresholds so you can course-correct early.
How can merchants minimize Enumeration attacks?
Visa does not disclose which transactions will be flagged as enumeration, as doing so could tip off attackers. The network likely uses internal models, possibly including the VAAI score, to identify enumerated transactions.
Merchants should use trusted vendors or build their own bot detection capabilities to identify this activity upstream.
If you operate in a high-risk Merchant Category Code (MCC), your likelihood of being targeted by bots is significantly higher. CAPTCHA may help in some cases, but often introduces friction for legitimate users. Instead, we recommend the following strategies:
- Use invisible form fields to catch bots. Add hidden fields to your checkout or login flows that are ignored by humans but often filled by automated scripts.
- Leverage invisible CAPTCHA solutions that detect emulators and bots based on device behavior. Some providers use on-device signals to flag automation without disrupting the user experience. See this blog for how Sardine approaches this today.
- Watch for high-risk traffic signals, such as spikes or unusual velocity in authorization attempts, especially concentrated against a single issuer, BIN, or a sequence of PANs. Strong bot detection may also allow for more flexibility in velocity thresholds used for customer declines.
- Review response codes for possible signs of bot behavior. Authorization declines with response codes that are indicative of potential bot attacks, including Response Code 14, which means Invalid Account Number or Response Code 54, which means Expired Card.
Our recent blog on zero-day signals explores advanced indicators that can help you detect emerging threats before they impact your authorization traffic or fraud rates.
How Sardine can help
Sardine helps fraud teams stay below VAMP thresholds by improving the speed, precision, and visibility of their fraud and dispute workflows.
Our platform is built to detect enumeration attacks in real time, using device, behavioral, and network-level signals that go far beyond static velocity rules. We surface risky authorization patterns early, so you can stop bots before they trigger chargebacks or policy violations.
Sardine also helps teams strengthen dispute resolution with integrated support for Compelling Evidence 3.0. We automatically collect and structure signals like device match, biometric consistency, and behavioral indicators to support strong fraud rebuttals through Order Insight.
For acquirers, Sardine offers visibility into merchant-level enumeration trends, dispute ratios, and fraud signals, making it easier to identify at-risk merchants and intervene before they cross enforcement thresholds.
Whether you’re trying to prevent double-counting, suppress TC40s, or detect bots before they escalate, Sardine gives you the tools to act faster and more confidently under VAMP.
Contact Sardine if you’d like to explore ways to manage card fraud and chargebacks.