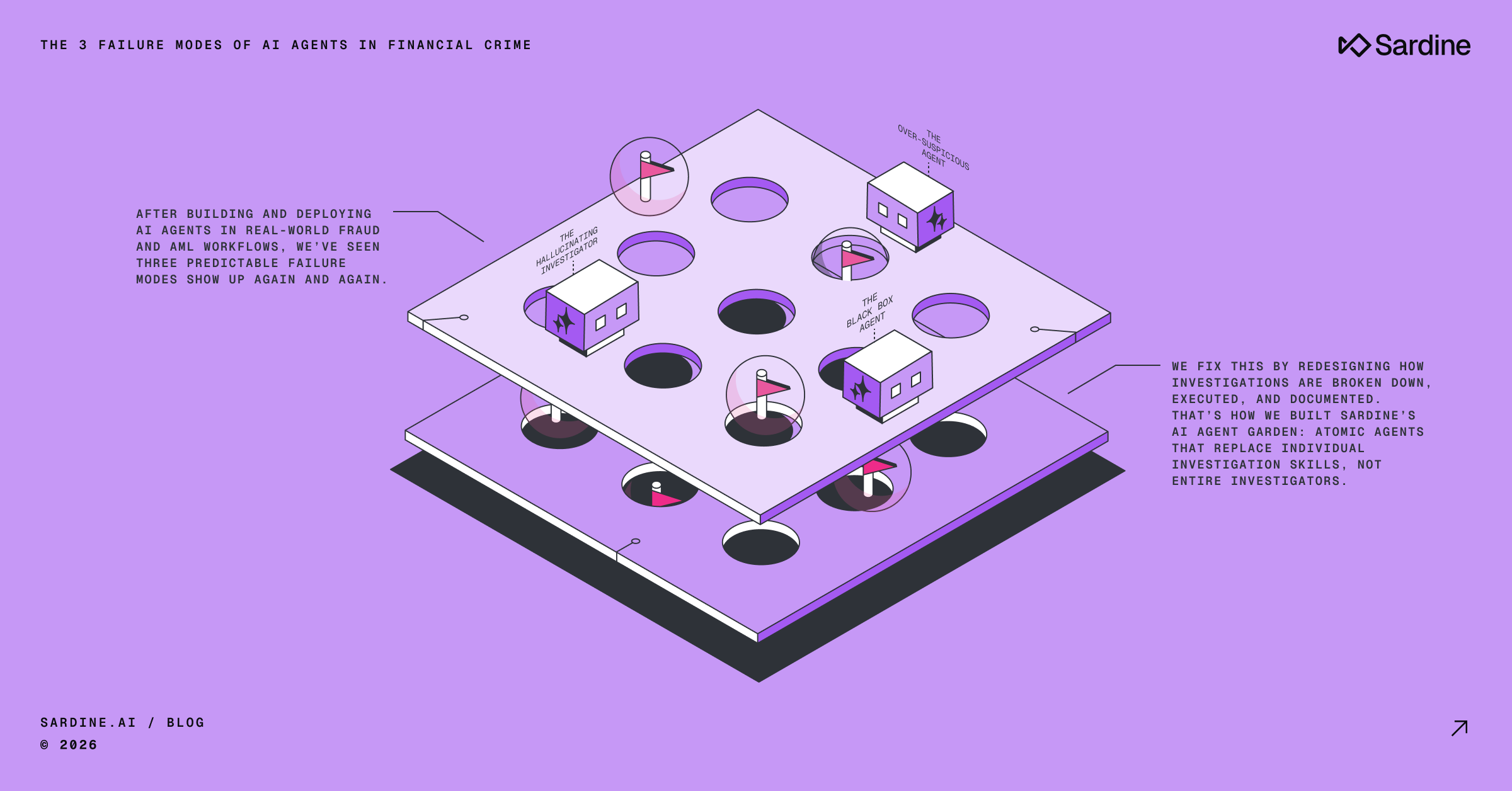
Detect more Account Takeover (ATO) with Sardine
Nearly 1 in 4 adults in the US have had their account taken over by a fraudster; since 2019, attacks are up 3x, and in 2021, losses increased by 90%.
Compounding this issue is that account takeovers (ATOs) are notoriously hard to detect effectively.
Detecting ATO often means Fintech wallets and merchants “step up” customers and add friction to the experience. This creates cost, reduces revenue, and frustrates consumers.
But there is a better way.
What is Account Takeover?
Account Takeover is when a fraudster accesses a genuine customer’s account. This attack can happen to any account email, social, subscriptions, bank, or credit card.
Once they have access to an account, they can make fraudulent transactions, use loyalty points, collect customer data to sell, and even change the password to lock the customer out.
To the merchant or Fintech wallet, these attacks often look like legitimate logins.
Why is ATO getting worse?

Following a wave of data breaches and the rush to digital and e-commerce during the pandemic, fraudsters became more creative. They began to operate at scale, overwhelming traditional approaches to ATO detection.
To the service provider, the account appears to have logged in with a legitimate username and password. This authenticated user may not trigger a fraud control unless the merchant or Fintech wallet is intentionally looking for things out of the ordinary.
We need to move faster to create a safer environment for users online.
How Do Criminals Get Your Account Information?
Step 1: Get a Password
The user/password is leaked from one of the breaches, and there is a good chance of the same password being reused by most of the victims at other sites.
Step 2: Get the OTP or “One Time Password”
The next step by the fraudster is to get any secure PIN codes your service provider might send you (for example, a one-time SMS code or email).
They have several attacks to get access to these passcodes (OTPs).
- Sim Swap attacks The attacker convinces a mobile phone network (like AT&T, Verizon or Vodaphone) to “port” the phone number to a new device. Then when the OTP passcode is sent, it would go to the attacker, not the victim.
- Phishing attacks Convince the customer to hand over OTP and can work two ways
a) Fake websites or emails: Fraudsters create websites, emails or invoices that look like a legitimate business that the customer works with and an account issue.
b) Intimidation: Using pressure or scare tactics against the customer to persuade them to share their OTP - Stolen Devices A device is stolen after the fraudster can see the mobile phone PIN or code used by the victim. By stealing the device, the fraudster can now receive an OTP email or SMS, which allows them to easily login to the customer’s provider (e.g., their bank or Fintech company).
- Malware Malware is software, an app that compromises the device when installed. This can be installed by clicking a bad link (like in Phishing) or delivered via spam and other adverts.
Step 3: Commit Fraud
Once the fraudster has access to the account, they can empty it, use it for illicit activity, or make purchases as if they were the user.And the Fintech wallet or merchant would only find out when the user contacts them.
Traditional approaches are not preventing ATO
One solution is to use device fingerprinting. Many merchants and service providers will use signals from the device, like browser settings or the mobile phone’s unique IMEI number to ensure a user is logging in from the device they used previously. If the device changes, the service provider will look for an additional layer of security, often called a “step up.”
In a Fintech wallet use case, users logging in from a new device may be asked to provide additional authentication (e.g., verifying with a code sent via email or SMS). This second authentication factor gives the service provider confidence they have a legitimate user.
With the explosion of account takeover attacks and volume, more good customers are getting caught by step-up 2-factor authentication.
These false positives create friction and frustration for users, creating cost and churn for Fintech wallets and merchants.
The need for fine-grained detection

Simply looking at the device and login event in isolation misses the bigger picture. To prevent more ATO fraud, organizations should.
- Combine device signals with behavior. Not all device signals are created equal, and fraudsters have figured out how to spoof locations and other key device signals. But when you combine smaller, often less considered device characteristics with how the device is being used (the behavior), you can detect more fishy behavior.
- Combine data sources to create better insights. Databases from 3rd parties include credentials known to have been hacked or mobile phone numbers that have historically been used for fraud elsewhere. Combine these with the device and behavior and build a complete picture.
- Detect remote software. Very few good users login to their accounts via remote screen-sharing software. For the fraction that does, the additional friction of step-up authentication allows them to log in successfully.
- Detect emulators. Almost no good users emulate their mobile device on a laptop or another device.
- Watch for anomalies across the entire customer base. With fine-grained device signals it is possible to see if multiple users and login attempts all have a similar pattern where something looks fishy.
- Implement a “Same User Score.” If a phone gets stolen or compromised by malware, the same user score allows merchants to detect risky behavior on the same device.
- Data Breaches. Proactively monitor other data breaches for your customers.
- Sim Swap. Identify potential SIM swaps through data feeds and anomaly detection.
Why Sardine is unique
Sardine can detect the hidden clues and signals fraudsters leave behind in an ATO attack and deliver significant reductions in ATO.
Across our client base, we’ve seen incredible results when they deploy the full power of Sardine. One client reported a 34.8% ATO reduction in the first month of implementing Sardine (and we continue to optimize).
But the real win was reducing false positives by 63.9%!
Less friction. More fraud detected.
Sardine was built to combine data sets with device and behavior. We have more fine-grained signals than the competition, which helps us detect fraud and reduce false positives.
Of course, we can’t tell you precisely how we do that (if you know, you know).
We’re about results.
And we’d love to help you get them.
If you want a demo, why not contact us?



%20(1).avif)